
Creating a SSL for your local Sitecore Site
When you install Sitecore, the installer will quite handily setup some SSL certificates for you. That way when you test locally your site will correctly run under https. However for various reasons you may not have used the installer to setup your local instance, in which case you need to do it yourself.
Creating a self signed SSL certificate however is one of those things that's always been far harder than is should. Previously I've written about how you can do it using mkcert, but recently I've found another way.
Creating a new self-signed SSL certificate with PowerShell
First open a PowerShell window or if you use the new Windows Terminal then one of those will do. Make sure you run it as an administrator or you'll run into permissions errors.
Then run the following command filling in your site URL and a friendly name.
1New-SelfSignedCertificate -CertStoreLocation Cert:\LocalMachine\My -DnsName "my-site.local" -FriendlyName "MySiteName" -NotAfter (Get-Date).AddYears(5)
This will create a cert with the expiry date set in 5 years time.
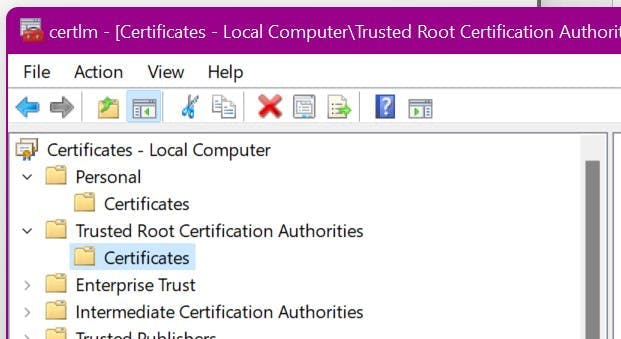
Next, it needs moving to the Trusted Root Certification Authorities store.
Click Start and type:
1certlm.msc
Find the certificate you just created in your personal certificates, and copy it into the trusted root certificates.
IIS HTTPS Site Bindings
To instruct your site to use the new certificate you need to update the IIS bindings for your site.
Go to IIS > selects site > Bindings... and then choose the https bindings.
You should have something like this.
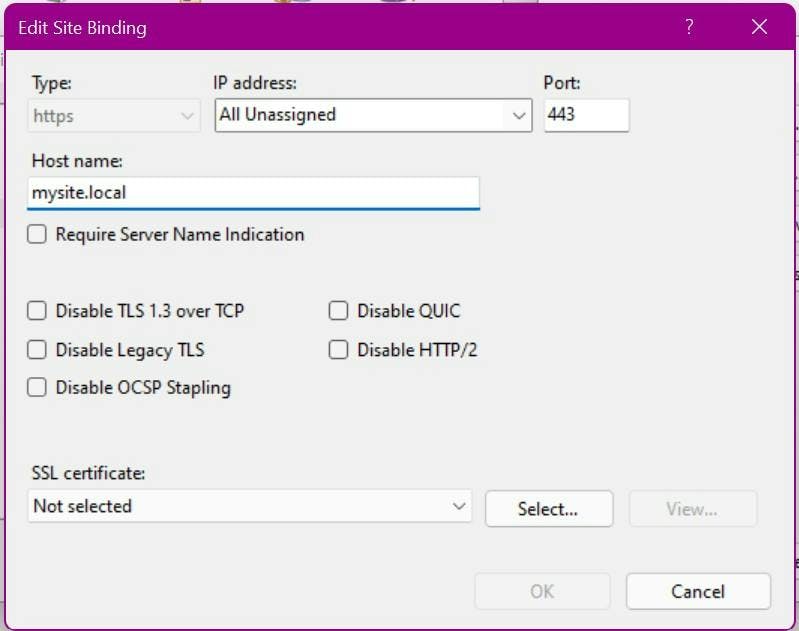
In the SSL certificate drop down, pick your newly created certificate.
At this point you should have an SSL certificate which browsers actually like!
Other Sitecore Settings
Despite the newly working certificate you may still run into issues with Sitecore which could either be due to SSL thumbprints in config files or config settings for URLs not including https. e.g. In {IDENTITYSERVER_ROOT}/Config/production/Sitecore.IdentityServer.Host.xml there is a setting for AllowedCorsOrigins which will need the https version of the url.

